In today’s digital landscape, data breaches pose significant risks to businesses, their customers, and their reputation. This blog post is designed to provide practical guidance to you on how to effectively handle data breaches in compliance with the EU General Data Protection Regulation (GDPR) and the new Swiss Federal Act on Data Protection (FADP).
Understanding data breaches
A data breach occurs when unauthorized access, disclosure, or destruction of personal data takes place. This unauthorized access could come from external threats like hackers or internal mishandling of data by employees. The consequences of a data breach can be detrimental, including financial losses, legal repercussions, and a significant blow to a company’s reputation.
Data breaches can take many forms, for example:
- Phishing attack: An employee falls victim to a phishing email and unknowingly provides login credentials to an attacker who gains access to the company’s database containing personal data.
- Lost or stolen devices: An employee’s work laptop or smartphone is lost or stolen, potentially exposing personal data to unauthorized individuals.
- Misdirected emails: An employee sends an email containing personal data to the wrong recipient due to a typographical error or confusion, thereby disclosing the data to an unintended party.
- Data backups compromised: Backup copies of data are not adequately protected, and cybercriminals gain access to these backups.
Handling data breaches under the GDPR
Privacy laws typically differentiate between data breaches when a company assumes the role of a data controller versus a data processor.
When you act as a data processor (e.g., you are a software service provider), you need to notify the respective data controller (your customer). On the other hand, the controller may need to notify – depending on the circumstances – the supervisory authority and/or the affected data subjects. The steps are the following:
If you act as a data processor
Data processors must inform the relevant controllers about the breach’s nature, scope, and potential consequences. When doing so, the following elements should be taken into account:
- Include all facts that are relevant to the breach (e.g., timeline, description of the breach, personal data affected, as well as data subjects, measures taken and proposed):
- The deadline for this notification is usually established in the data processing agreement between both parties and very short – typically between 12 and 48 hours. Data processors thus need to be able to notify the affected controllers within that short timeframe after being aware of the breach. This can be a challenge, especially during weekends and public holidays – all the more important to be well prepared and know who to inform.
It is also essential to bear in mind that if you act as a data processor, you should not notify data subjects or the supervisory authority, as that is the responsibility of the data controller.
By ensuring an effective and timely notification, data processors allow data controllers to take necessary actions to mitigate risks and ensure affected individuals’ rights are upheld. It also fosters your credibility as a trustworthy contractual partner.
If you act as a data controller
If the data breach occurs at the data controller, the controller may need to notify the relevant supervisory authority and/or the affected data subjects. Transparency is key, and communication should include information about the breach’s scope, potential impact, and steps taken to mitigate risks.
The responsibilities data controllers are subject to are:
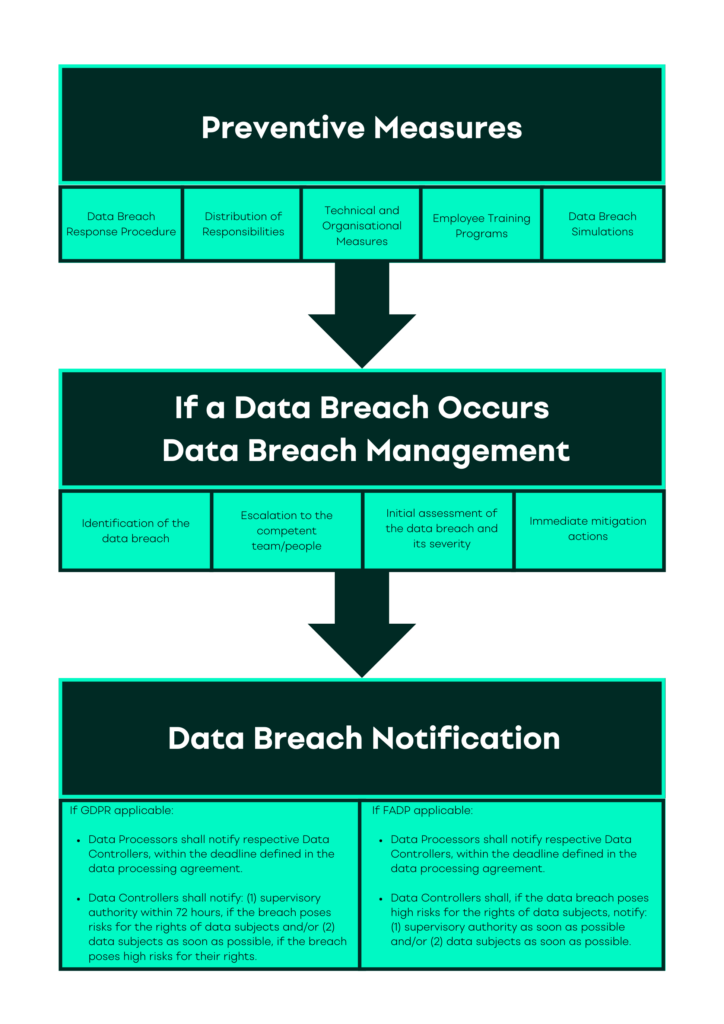
- Notification to the supervisory authority: You have to notify the authority if the breach is likely to result in a risk to the rights and freedoms of natural persons (based, e.g., on the potential damages caused to data subjects, sensitivity of the affected personal data, mitigation actions taken and their efficacy). This must be done within 72 hours of becoming aware of the breach.
- Notification to data subjects: Additionally, there may be a need to notify affected data subjects if there is a high risk for them derived from that data breach unless the controller has implemented necessary technical and organizational protection measures to the affected personal data or it has implemented subsequent measures which ensure that the high risk is no longer likely to materialize (for example because the data is encrypted). If necessary, this notification should be done as soon as possible after becoming aware of the breach.
Handling data breaches under the FADP
The essential steps you need to follow when managing data breaches under the FADP are in most part identical to those of the GDPR, with some minor differences that are the following:
If you act as a data processor
Similar to the GDPR, the FADP distinguishes between data controllers and data processors. Thus, the processor is subject to the same notification obligation to the relevant data controller as in the GDPR, especially based on the terms of your data processing agreement (see above).
If you act as a data controller
Under the FADP, you may be required to report data breaches to the Federal Data Protection and Information Commissioner (FDPIC or EDÖP), as well as to the data subjects if you identify a high risk to data subjects’ fundamental rights. The main differences to the GDPR in this regard arise from two facts:
- Whilst the GDPR establishes a period of 72 hours to contact the supervisory authority, the FADP only requires data controllers to proceed the notification as soon as possible.
- A notification to the authority is only necessary if a high risk for the data subject occurs while under GDPR, every data breach with a risk for the data subject needs to be notified to the authorities.
Best practices for data breach prevention
In order to mitigate potential data breaches and negative consequences for the company, as well as for the affected data subjects, it is advisable to adopt measures to avoid their occurrence. The most important measures are:
- Data breach response procedure: Companies should adopt a comprehensive incident response plan that outlines preventive measures and detailed procedures to follow in the event of a data breach. If a data breach happened, the last thing you want to think about is setting up a new procedure ad hoc.
- Distribution of responsibilities: Crafting an incident response plan and managing data breaches in an efficient way involves appointing a team responsible for data breach management. This team should include representatives from legal, IT, communications, and relevant departments.
- Prevention is better than cure – technical and organisational measures: Companies must continually assess and update their security measures and controls to align with evolving threats. Implementing encryption, access controls, and intrusion detection systems fortifies defences against potential breaches. Regular security audits and vulnerability assessments help identify weaknesses and reinforce protective measures.
- Employee training and awareness programs: Educating employees about data protection practices and data breach response protocols is key. Conduct regular training sessions to enhance employees’ awareness of potential threats and equip them with the knowledge to identify suspicious activities.
Conclusion
Navigating data breaches under EU and Swiss privacy laws requires a proactive and informed approach. By understanding the intricacies of breach management, communicating effectively, and implementing preventive measures, you can protect both your data and your reputation. We recommend the following:
- Develop an incident response procedure: Create at least a basic incident response plan that outlines responsibilities, immediate actions, and communication protocols to ensure a coordinated response to data breaches.
- Appoint a dedicated team: Designate a specialized team comprising legal, IT, communications, and relevant department representatives to manage breach incidents efficiently.
- Prioritize security measures: Implement robust security measures such as encryption, access controls, and intrusion detection systems to fortify defenses against breaches.
- Educate employees: Provide regular training sessions to educate employees about data protection practices, data breach identification, and appropriate response actions.
- Promptly notify data controllers, supervisory authorities and data subjects: Ensure an efficient and timely notification to the relevant third parties when data breaches occur, to comply with GDPR and FADP provisions.
We know that each situation is unique, and we’re here to discuss yours in detail. Please don’t hesitate to book a free call with our privacy experts.